Scenario :
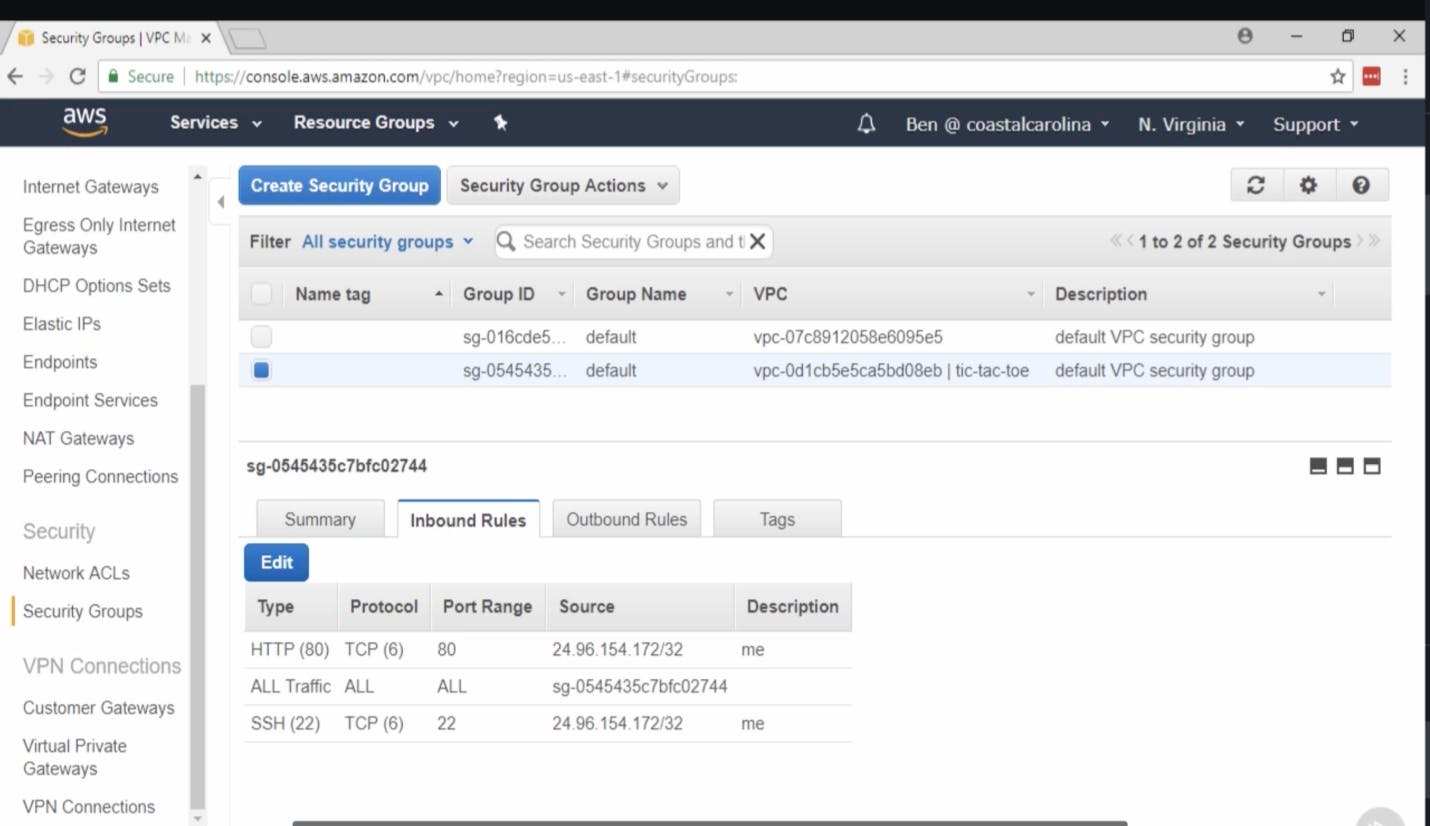
Let's say We have an inbound rule that allows HTTP traffic into the instance from our IP address.
 All right, let's jump back over to the Outbound Rules tab. Again, there is no rule explicitly allowing an outbound connection to our IP address.
All right, let's jump back over to the Outbound Rules tab. Again, there is no rule explicitly allowing an outbound connection to our IP address.
 will the security group allow the reply traffic to go out? i.e If we jump over to Chrome and type in the public IP address of the instance and attempt to browse to it will it work?
will the security group allow the reply traffic to go out? i.e If we jump over to Chrome and type in the public IP address of the instance and attempt to browse to it will it work?
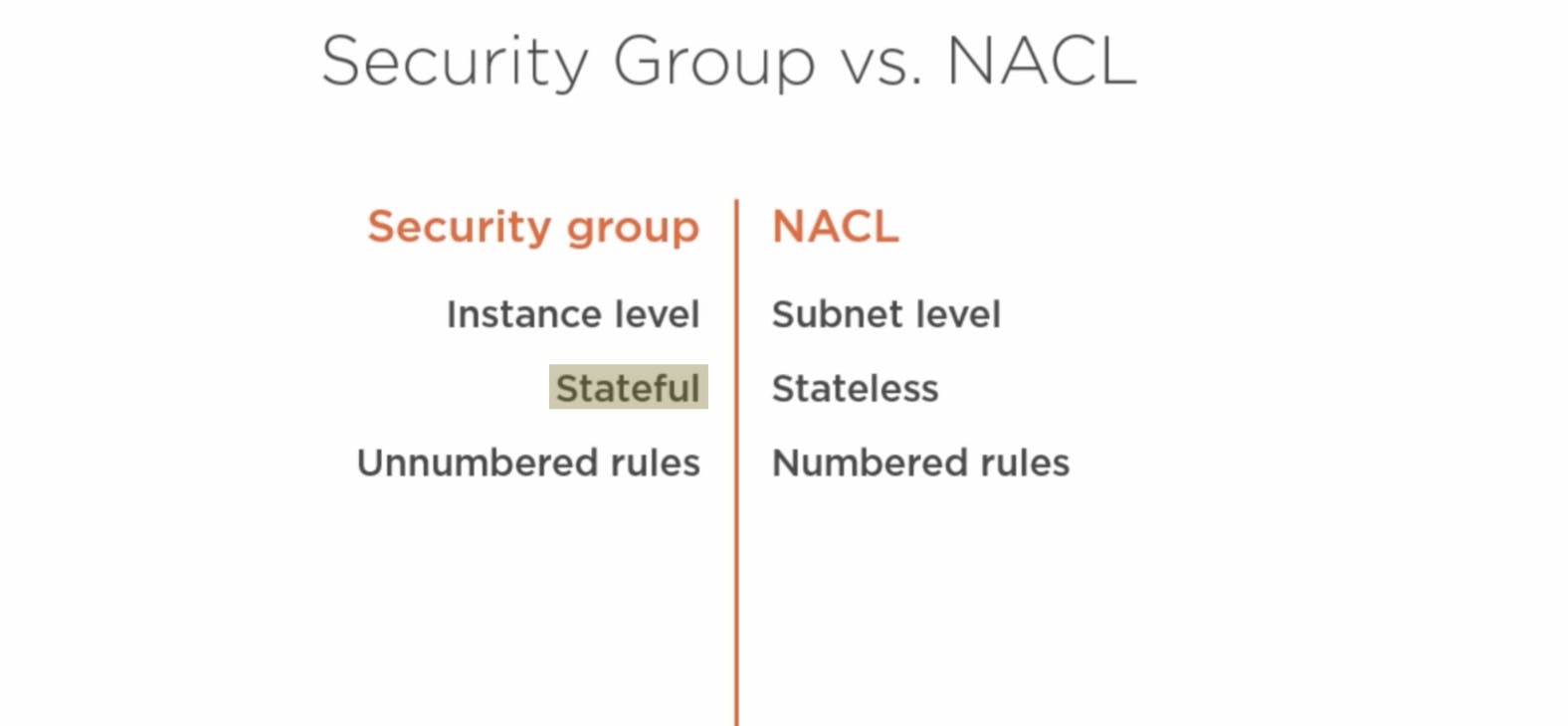
How security groups actually work - stateful behaviour
Security groups are what's called stateful because they track the state of the connections to and from your instance. What this means is that if you allow traffic into your instance, which is what we are doing here with this rule, the security group will automatically allow the instance to reply to that traffic, even if there is no corresponding outbound rule.
Because the inbound rule allows traffic in from our IP, the stateful nature of the security group will allow the reply traffic to go out.
Let's verify that we cannot get to the internet via an ssh session. Let's try to ping 8. 8. 8. 8, in the ssh terminal of instance, and it does not work. We have no outbound internet access. All right, and that's what we expect.
Now, let's access the application by browsing the public IP address of the instance, and yes, indeed, we are able to browse to the app. Why is that? Well, again, it's because those security group rules are stateful. Even though we removed the outbound rule allowing internet access, we still kept the inbound rule that allows connectivity into the instance.
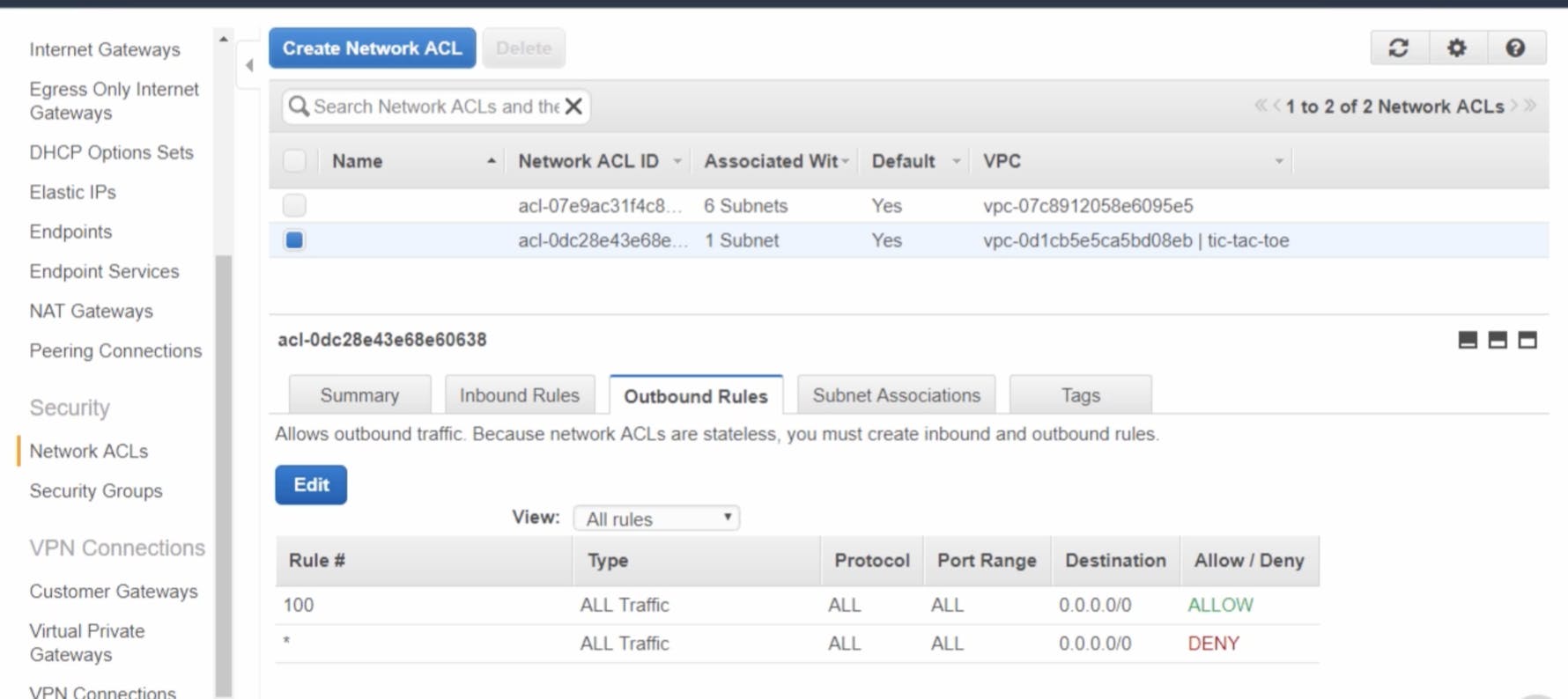
Then what about NACL
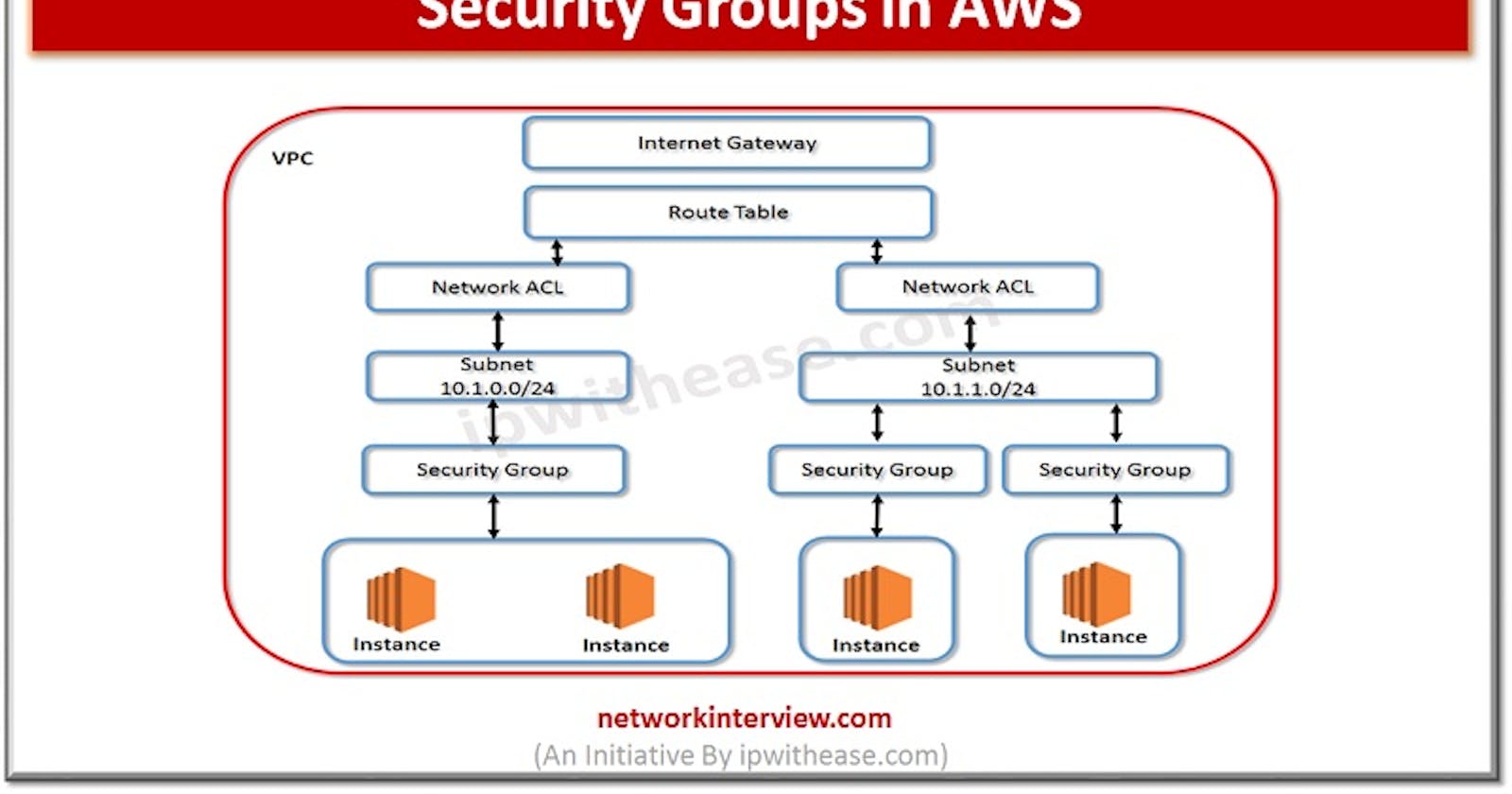
NACL is similar to security groups as well, but which gets applied at the subnet level. It needs explicit allow/deny statements and unlike security groups, it won't allow reply traffic. i.e we won't able to access the application if there is deny in outbound traffic